Spear Phishing
One of the methods used by scammers is to impersonate someone from your own domain name. E.g. you get an email from accounts@yourdomain.com.au asking you to open email attachments or click links.
To combat this is easy, stop allowing them from using your domain name in the first place!
Stop the Spear Phishing
Simply enable DKIM, DMARC and SPF. That’s a lot of acronyms you say? Don’t worry this article will tell you how to do it.
For the technically minded, DKIM is simply a process of locks and keys. When you send an email to someone, the email header is encrypted with your private key. The receiving email server then decrypts the header using your DKIM public key. If decryption is possible, then the server knows that the email is genuine and 100% from yourdomain.com.au
Prerequisites:
- An active Microsoft 365 subscription with Custom email domain already configured
- Access to your DNS hosting provider
- First log into your Office365 workload in Powershell as Administrator
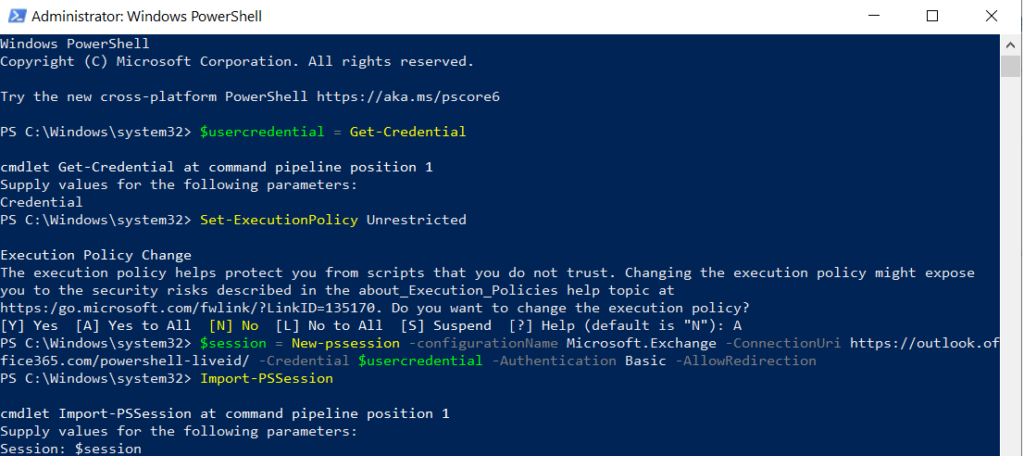
- Determine your DKIM session keys:
Get-DkimSigningConfig -Identity | Format-List Selector1CNAME, Selector2CNAME
- Log into your DNS hosting provider
- In this example we are using Synergy Wholesale in Australia, edit your domain
- Create 2 new CNAME records
selector1_domainkey. IN selector1-yourdomain-com-au._domainkey.[tennantaccount].onmicrosoft.com TTL 3600
selector2_domainkey. IN selector2-yourdomain-com-au._domainkey.[tennantaccount].onmicrosoft.com TTL 3600
E.g. selector1-itnetworks-com-au._domainkey.itnetworks.onmicrosoft.com
- Create a TXT Record
_dmarc. IN v=DMARC1; p=reject TTL 3600
- Now head over to your Office365 Exchange Admin > Protection > DKIM
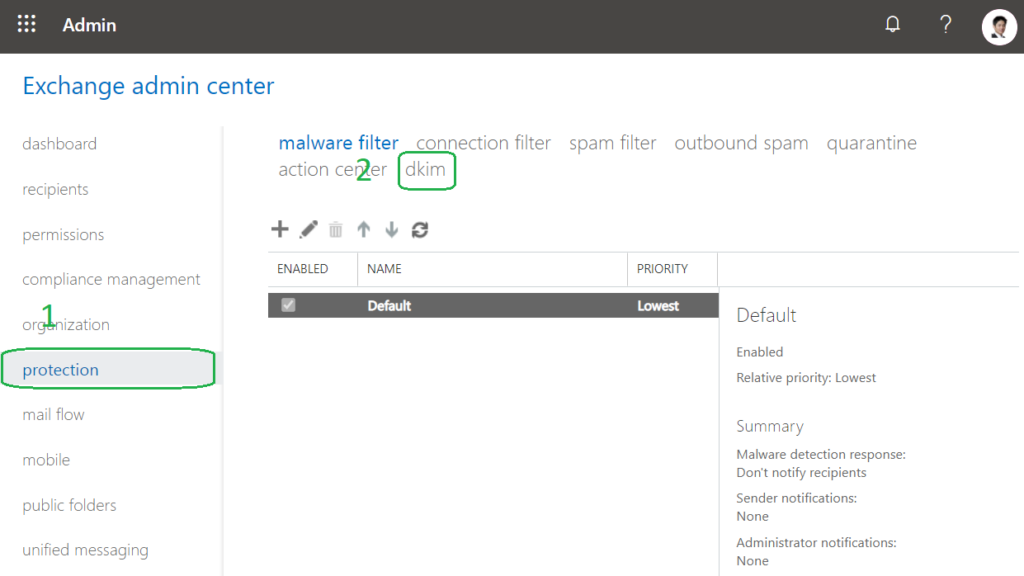
- Select your domain from the list then click “Enable”
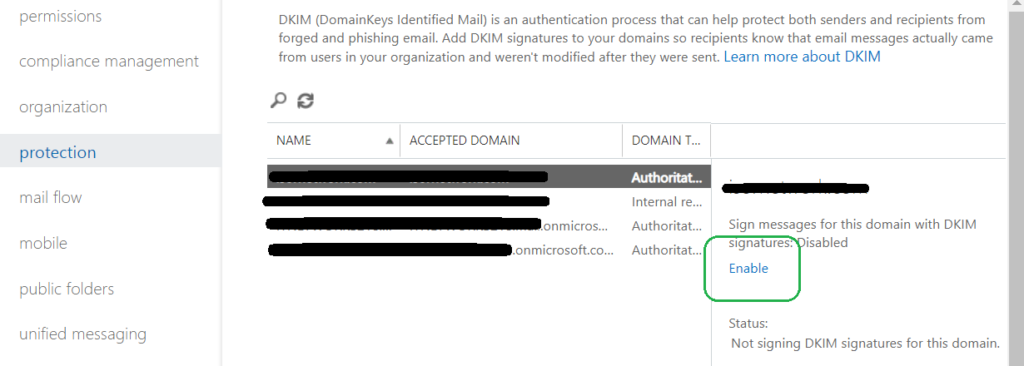
- Wait for your DNS changes to take affect.
- Head over to https://dkimvalidator.com
- The website will provide a random email address to send an email to. Send a test email to that address.

- Wait a few minutes for the address to transmit, then click “View Results”
- What you are looking for is a DKIM result of PASS.
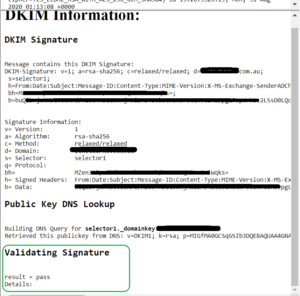
If you have followed this far then your email domain is now protected from being ‘used’ by others. As with all our guides, please feel free to reach out if you need help with any of this.


