Ransomware is on the rise!
Here is Part 1 of a series of articles on how you can prevent your organisation from having your data locked up. These guides can, and should, be done now!
The Ransomware ‘process’ usually comes in email via attachments that are executed (opened by the user). However, we usually find that the attacker has already gained access to the system before the Ransomware attack is performed.
Once the attacker has gained access they will:
- Collect data for a few days first, determine who are the best targets to attack (typically finance users)
- Copy/download company files
- Run password capture tools on the network such as Minikatz.
- Remove Windows Server backups and Shadow copies.
Once the above is done, the ransomware is invoked. We find that it is usually run on weekends and afterhours, when you have least chance of recovery.
In Part 1, we will disable the Windows Script Host and PowerShell. Users do not typically require these tools.
Restrict PowerShell
- Create a new Group Policy (Group Policy Management)
- On the Policy head over to User Configuration > Windows Settings > Security Settings
- Create a new Software Restriction Policy
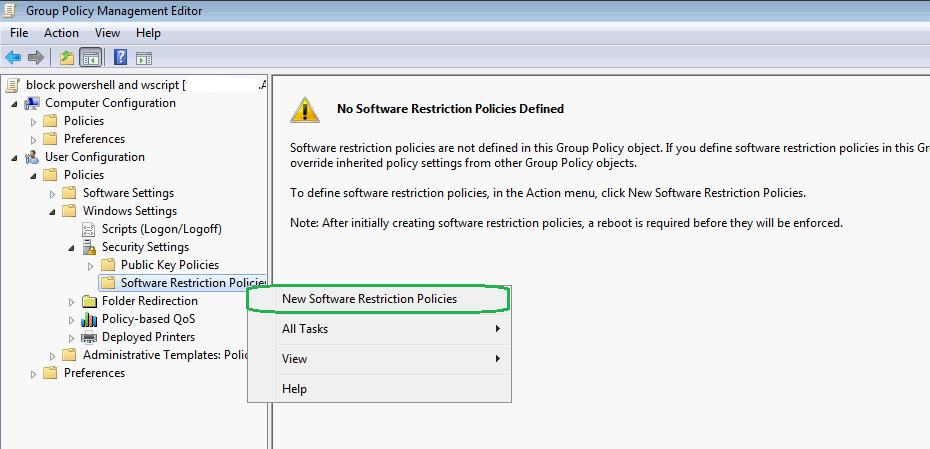
- Create a new Path Rule
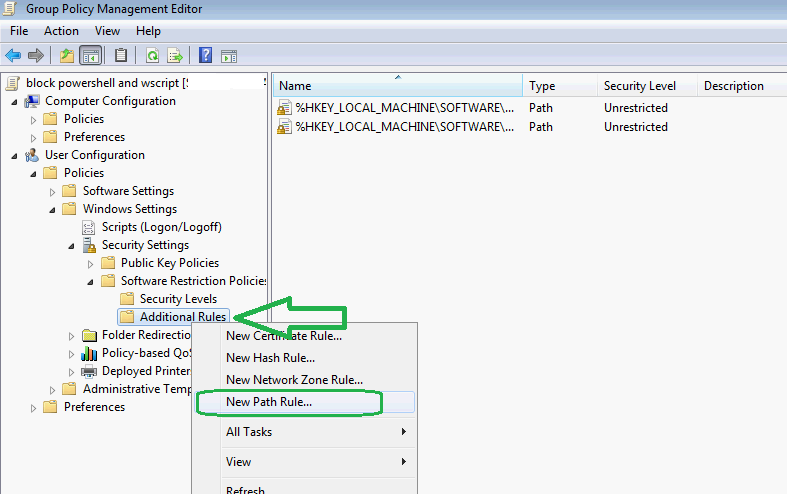
- The typical path for PowerShell is c:\windows\system32\WindowsPowerShell
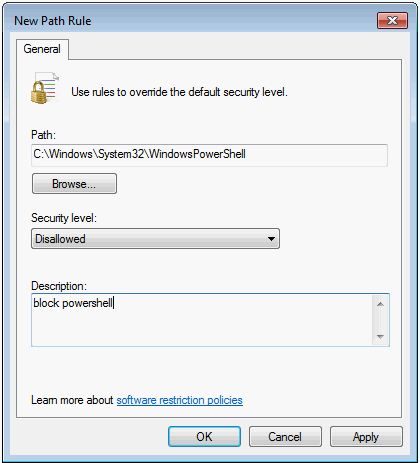
- Hit OK when done
Restrict Windows Scripting Host WScript
- On the same Group Policy from above, expand Computer Configuration > Preferences > Windows Settings
- Create a new Registry Item
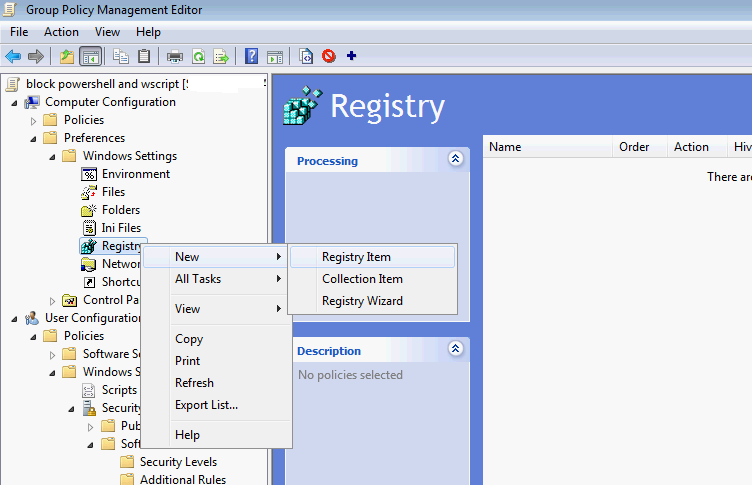
- Create a Registry entry as per below:
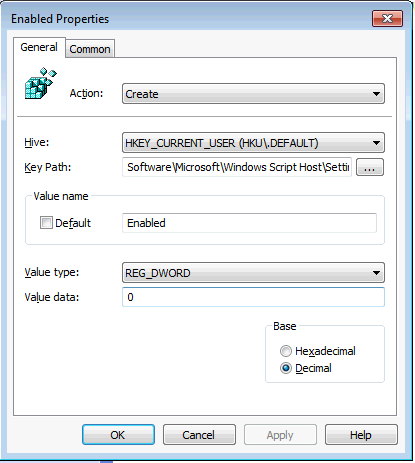 The Key path is Software\Microsoft\Windows Script Host\Settings\ You need to create two Keys, HKCU and HKLM
The Key path is Software\Microsoft\Windows Script Host\Settings\ You need to create two Keys, HKCU and HKLM


