IT Security Fundamentals
IT Security is all about keeping your data secure. In very simple terms, your data should be accessible to those who have been granted access and not accessible to those who should not have access. Sounds quite simple doesn’t it?
There are many facets of IT Security that need to be considered. This blog builds on the previous IT Security 101 article and focuses on keeping hackers away from your data by discussing how they can potentially compromise your system through vulnerabilities.
Patching Applications
Software companies regularly release patches for the operating systems and applications that they create. These patches can contain various types of updates to their software which may include enhancements, bug fixes and most importantly, security fixes.
If your systems and applications are not being regularly patched, you are at risk to any security vulnerabilities that may exist in the system or application that you are using. These security updates are best described as vaccines for the various known vulnerabilities that exist.
How vulnerabilities are exploited
All of the major software developers release patches and updates for their software. There is a web site called Common Vulnerabilities & Exploits (CVE) that lists and tracks all publicly known cyber security vulnerabilities. Microsoft also have their own site called Microsoft Security Response Center (MSRC).
Once an issue is known, the developer of the software will release a security patch or update for that particular issue or what is called a “roll up” update to address various issues in a single package. In a perfect world, these patches will be released before the vulnerability is made public.
If your systems are not regularly patched, you are susceptible to the vulnerabilities that exist. These can be as insignificant as a hacker being able to obtain a history of every web site you have visited or as extreme as being able to take complete control of your computer.
You can be exploited by receiving and opening an attachment to an email or even by visiting a malicious web site. How you can be exploited and the level of damage that can be done comes down to the nature of the vulnerability and the actions you have taken to mitigate the risk.
Web Browsers
Everybody these days uses a web browser to browse the internet. Browsing the internet can mean anything from researching a specific topic through to moving money around using internet banking.
The web browser has become a common target for hackers because of the value of the attack can be very rewarding.
If you visit a malicious web site, that web site is capable of exploiting any vulnerabilities your web browser may have. You are interacting with that site through the web browser on your computer. If your web browser is compromised, your computer can then be attacked.
Anti-virus
Anti-virus software can help you mitigate some exploits. Just like your patching needs to be up to date, it is just as important for your anti-virus software to be up to date. If your anti-virus software is not monitored and up to date, it’s the same as not installing security updates and patches.
Web Protection
Web Protection monitors the web sites you are visiting and blocks any known malicious sites. We recommend everyone has web protection activated as it is a great aid in enforcing company security policies.
Unlike patching and anti-virus, web protection uses an online database of known malicious web sites, IP Addresses and URLs. Any known problem destination is automatically blocked and the user receives a message similar to the one below when visiting such a site:
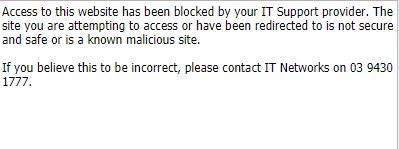
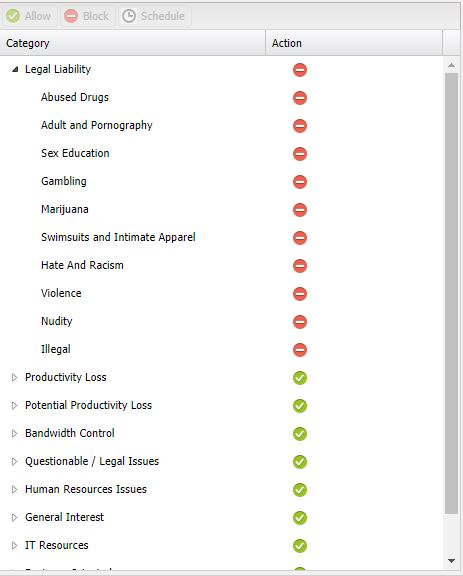
In addition to enforcing security, most web protection software can enforce blocking of sites based on site category. This can be configured to reflect a company-wide policy which has proven to be very effective in policing non business related internet traffic.
IT Security Implications
Not having effective anti-virus, web protection and your systems and applications patched, puts you at significant risk of becoming a victim. A potential hacker does not need your username or password to access your data or compromise your systems. It is just not worth the risk to not be diligent with your IT Security.
As always, we are here to help. Please contact us for any advice you may require.


