
Updated: 20/08/2020 – Since the beginning of August, 2020 there has been a sharp rise in the number of phone call scams where the caller will try to convince you he represents you IT Department or a known company such as Telstra. Scam emails share many of the same traits as a scam call so we’ve updated this article to include them too.
What is a Scam or Phishing Attack?
A scam is just a scheme to gain something from you fraudulently, most commonly your identity or money. Phishing is a type of scam that fishes for the information a scammer requires to get want they want. A Phishing scam will usually be an email, text or phone call that appears to come from a legitimate source. The scammer is hoping you will not notice it is illegitimate and provide them with your information.
At this point, I’d like to also clarify the term “spam”, as many people still find it confusing. The goal of this article is to give you a clear understanding of the terminology so that you can stay alert to what constitutes risk.
So, “spam” is defined just as annoying or repetitive, and usually uninvited email (or regular mail for that matter), texts or calls. It is not necessarily malicious. Whereas a “scam” is also uninvited but malicious in its intent to defraud you. You need to know how to spot them.
Warning Signs you are being Phished
Receiving an unexpected email, text or call that asks you to login, or provide login details, to a service such as your email, online banking, or any other site you have you have protected with a password, should immediately raise red flags.
Here are a couple of things to look out for that will confirm if you are being scammed:
Email:
- Look at who has sent the email to you. Most importantly, the email address that the sender has used, not just the name. For example:
From: IT ADMINISTRATIVE DESK <minna@tsubasa-f.or.jp>
It may well say it’s from “IT ADMINISTRATIVE DESK” but the email address minna@tsubasa-f.or.jp is who actually sent it to you. - All scam emails will want you to click on something that will take you to a logon screen so you can provide your username and password. Hovering your mouse over the link they want you to click on will reveal where the link will take you.
For example, the image below is trying to convince you that Microsoft have sent you a notification but by hovering over the link you can see it will take you to a google site that has nothing to do with Microsoft.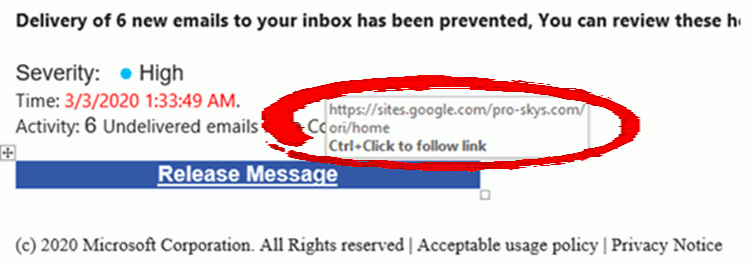
- Spelling mistakes and poor grammar are also common in most scam emails. Scammers may be poorly educated or English may not be their first language. Scam attacks are becoming more and more sophisticated every day though.
- Look for things that don’t match. An email from Australia Post or Microsoft will come from “auspost.com.au” or “microsoft.com”, respectively, – if the domain doesn’t look right, don’t trust it.
Text/SMS:
- Anything that provides a link or asks you to sign in to something. I cannot think of any services that uses text/SMS in that manner. I would treat any unsolicited text message as suspicious
- Anything offering you something for free! Most of the text/SMS scams seem to offer a free booklet, an amazing opportunity to boost your salary or other things that are probably too good to be true.
- Messages that are sent from hidden numbers. If the text comes from a name and you cannot see the mobile number, treat it with unabashed suspicion.
- Unsolicited text messages that do not include the option to Opt Out. Most legitimate organisations allow you to send STOP or something to be removed from their mailing list.
Phone Call:
- Unsolicited support calls from a “Technician” or “Engineer” claiming to have found a problem with your computer. You should probably know if your IT people are managing your device – if you aren’t paying for a managed IT Service – no one is monitoring your PC! If you are at all suspicious, ask to call them back – most of them will hang up on you or try and avoid giving you a way to contact them.
- Any “IT” person that asks you for your password. We just don’t do it. There is no reason for us to. If I need access to your account to resolve a problem I can reset your password, do what I need to do and then give YOU the new password. If someone asks for your password – just hang up.
- Like the emails and text scams, anyone that calls you with an amazing an unexpected offer that seems too good to be true – because it probably is!
- Related to the first point, any one that calls and tells you they need you to run an application or go to a web site that allows them to remotely access your computer to “fix a problem”. Again, if you pay for a managed IT service you will probably know about it. It’s expensive to have engineers sitting in their office monitoring and managing client workstations. If it wasn’t – I’d be out of business! Granting someone you don’t know access to your PC is like handing a stranger the keys to your home!
Conclusion:
Even the most cautious person can have a bad day and be tricked by a well-executed phishing attack. If someone manages to hold of your email address and password they will immediately start using that combination to try and log in to other sites knowing that many people use the same email/password combination in multiple places.
They may change your password and lock you out of your own account. Or add rules to your mailbox that forward them copies of any mail you send or receive. It depends on how serious the attackers are, what they manage to get access to and what they are after.
The best way to stop you from becoming a victim is to be protected with Multi-Factor Authentication (MFA) wherever it is available. Even if you give up your username and password, your account cannot be accessed without your consent as the second factor of authentication is required.
And if you don’t have anyone managing your IT then you can, of course, call us.


