IT Security Fundamentals
IT Security is all about keeping your data secure. In very simple terms, your data should be accessible to those who have been granted access and not accessible to those who should not have access. Sounds quite simple doesn’t it?
However there are many facets of IT Security that need to be considered. This blog focuses on the most fundamental: ensuring you know who is accessing your data.
Authentication
To ensure your data is secure, anyone attempting to access it should be providing a username and password to authenticate their identity before they are provided with access. If a username and password is not being used then there is no way of administering or auditing access. Every time a login is attempted, the event should be recorded into an event log so there is an audit trail of who has been accessing the data. More importantly, failed access attempts should also be recorded so you are aware of any suspicious activity and can take action against it.
If your systems, applications or storage facility does not provide that basic functionality then you are asking to be compromised and won’t even know you have been hacked.
Strengthened Authentication
Basic authentication, as previously described as a username and password is the bare minimum that needs to be implemented. Even with basic security in place, hackers will attempt to continually logon and compromise whatever security you have in place. There are various tools available to hackers that will allow them to automate the login process until the username and password combination is cracked. One of the most popular attacks is a brute force or dictionary attack.
One way to mitigate against dictionary or brute force attacks is to lock out accounts after successive failed login attempts. Once an account is locked out, the legitimate user cannot logon until the account is manually reactivated.
A better way of mitigating against any attack is using Multi-Factor Authentication (MFA). Having your users enabled with MFA will provide you with a very high degree of confidence in who has access to your data. We talk more about using MFA in our Protect Your Business With MFA article.
Where to use what
The general rule of thumb is “any authentication method that can be accessed through the Internet and is unsecured, should be secured with MFA”. Common systems that are accessible on the Internet are online accounting packages, Microsoft 365 and online Customer Relationship Management (CRM) systems. All should have MFA enabled.
Internal systems, such as office PCs do not necessarily need to be protected with MFA. Any system or device that can only be accessed by physically being in front of it, generally does not need MFA.
Microsoft 365 IT Security
There are various things that can be done to a Microsoft 365 subscription that can greatly strengthen the basic security that the subscription comes with out of the box. MFA is the most obvious, as previously discussed. In addition to MFA there is Geo blocking that only allows login to Microsoft 365 from the country or countries you configure. Microsoft 365 also the ability to customise or “brand” the Login Screen with your company logo.
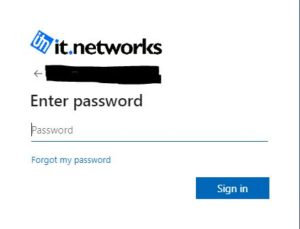
The login screen above clearly shows that I am logging into the IT Networks Microsoft 365 portal as our company logo is clearly displayed. If I do not see our logo I know that something is untoward and I would not enter my password.
IT Security Implications
Not having your systems, applications or storage adequately secured can have significant consequences. Everything these days is Internet connected. Apart from the inconvenience, you could have your identity stolen if your email is compromised. You could have your entire customer and prospect database stolen by a competitor if your CRM is compromised. You could be financially impacted if any of your data or applications are compromised. It is just not worth the risk to not be diligent with your IT Security.


