Ethical Phishing
Microsoft365 has a awesome new capability to send phishing emails to your users! Why would you want to phish your own users? Well its a great way to determine which users in your organisation need further training in identifying dodgy emails.
How to phish your users:
- With your tenant account ready, headover to https://security.microsoft.com
- Click on Attack Simulation Training
- Click on Attack Simulation Training
- Launch a simulation
- Choose the type of simulation you want to inflict on your users, for this example we are going to do a Credential Harvest and attempt to trick the user into giving us their password!
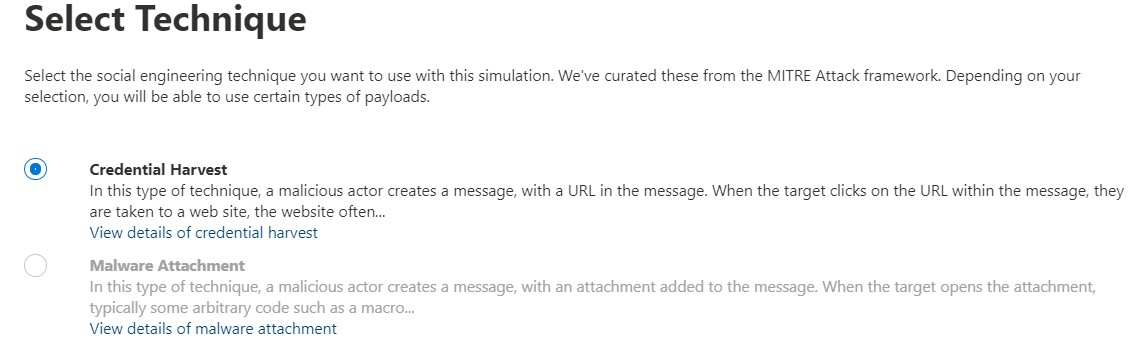
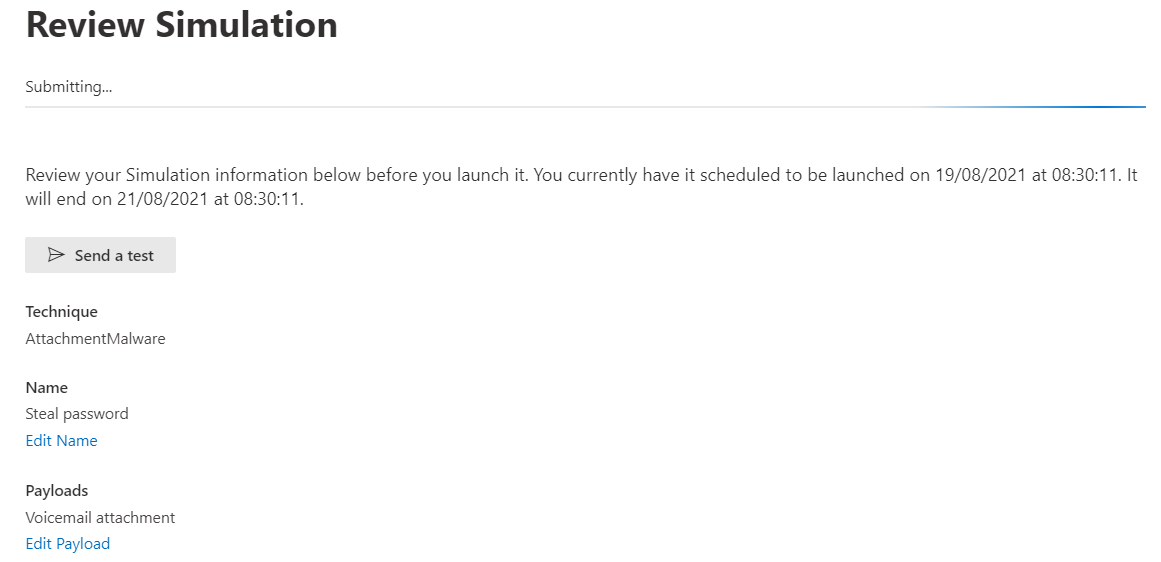
- Give the simulation a name, such as ‘steal passwords’
- Select a payload, A payload in this simulation is the email the user will receive
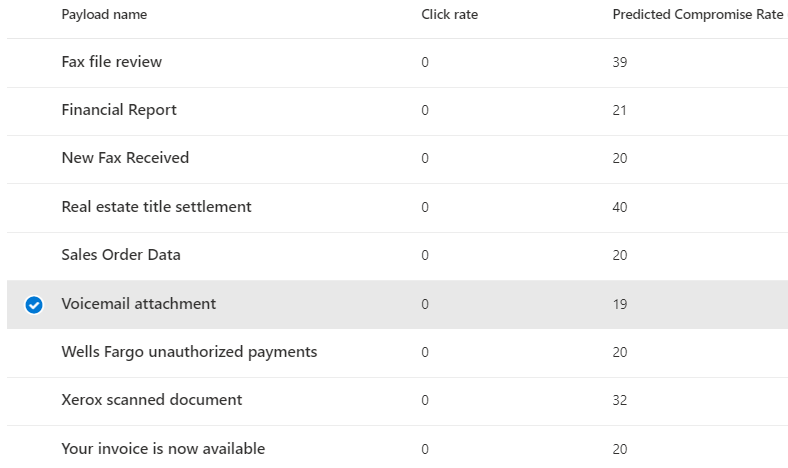
- Choose who you want to target, a good idea is to test it on a few people at a time.
- Should the users selected fall victim to your nasty trick, you can provide them with training to hopefully help them identify such dodgy emails next time.
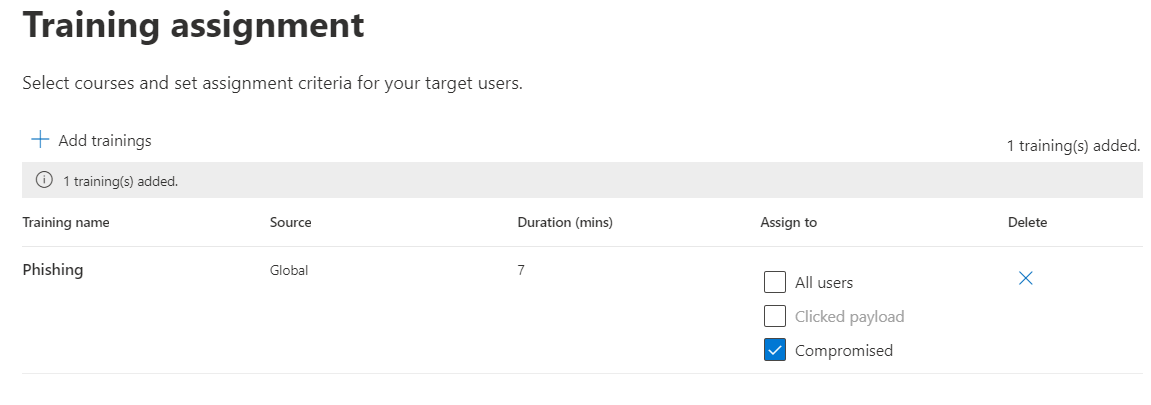
- Review your simulation and let the games begin!
The Aftermath
After the simulation has run the users will receive the email with payload attached: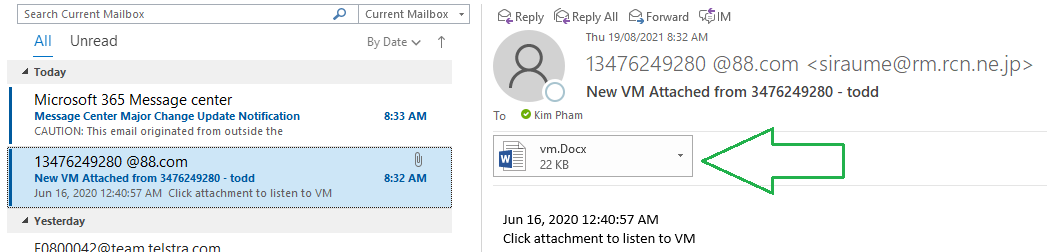
Hopefully no users will fall victim to your simulation, should some users launch the payload, its a good idea to follow-up with with related training. For extra points run another simulation and specifically targeted these users, you will notice it is always the same users that like opening and launching any email, file they can get their hands on!!!


