
How much does a cyber audit cost
In an era where cyber threats continue to evolve in sophistication and frequency, safeguarding against potential breaches and attacks is paramount for businesses operating in Australia. The Australian Cyber Security Centre (ACSC) has outlined a set of baseline security strategies known as the Essential Eight, designed to mitigate the risk of cyber incidents. However, achieving compliance with these standards often involves conducting a cybersecurity audit, raising questions about the associated costs. In this blog, we’ll explore the intersection of cybersecurity audit costs and Essential Eight compliance in Australia.
Understanding the Essential Eight
The Essential Eight is a cybersecurity framework developed by the ACSC to assist organizations in enhancing their resilience against common cyber threats. It comprises eight strategies focusing on the mitigation of cybersecurity incidents, including:
- Application Whitelisting: Limiting the execution of unauthorized software to minimize the risk of malicious code execution.
-
Patch Applications and Operating Systems: Regularly applying security patches to address vulnerabilities in software and operating systems.
-
Configure Microsoft Office Macro Settings: Mitigating the risk of macro-based malware attacks by configuring Microsoft Office macro settings appropriately.
-
User Application Hardening: Implementing security controls to reduce the attack surface of applications commonly targeted by adversaries.
-
Restrict Administrative Privileges: Limiting administrative privileges to essential users to minimize the impact of potential security incidents.
-
Patch Operating Systems: Regularly applying security patches to address vulnerabilities in operating systems.
-
Multi-factor Authentication: Enhancing authentication security by requiring multiple forms of verification for access to sensitive systems and data.
-
Daily Backup of Important Data: Implementing regular backups of critical data to facilitate recovery in the event of a cyber incident.
Example of how much a Cybersecurity audit in Australia may cost
While prices depend on many factors including the size of an organization, an example of costs for an organization with 50 users and 1 Tb of data, the total cost comes to $8,800 when considering all audit stages.
Breakdown:
- Data Breach Risk: $1,800
- Vulnerability Risk: $4,800
- Security Policy Review: $2,200
Keep in mind, the total cost may vary depending on whether your organization requires all three steps. Some clients we’ve worked with skip the Data Breach Risk analysis if they already know their data types. If needed, use $50 per device and $100 per user as estimates for Data Breach Risk and Vulnerability Risk, respectively.
The Cost of Cybersecurity Audits
While implementing the Essential Eight strategies is crucial for bolstering cybersecurity defenses, achieving compliance often necessitates conducting cybersecurity audits. The costs associated with these audits can vary depending on several factors:
-
Scope and Complexity: The size and complexity of the IT network significantly influence audit costs. Larger networks with diverse infrastructures, multiple endpoints, and complex configurations may require more extensive audits, leading to higher costs.
-
Regulatory Requirements: Compliance obligations mandated by industry regulations or contractual agreements can impact audit costs. Organisations operating in highly regulated sectors such as finance, healthcare, or government may face additional compliance requirements, contributing to higher audit expenses.
-
Engagement Model: The choice of engagement model for conducting cybersecurity audits can influence costs. Some organisations opt for in-house audits conducted by internal cybersecurity teams to minimize expenses, while others prefer outsourcing to specialised cybersecurity firms for comprehensive assessments and expertise, albeit at higher costs.
-
Expertise and Tools: The expertise of auditors and the use of specialised tools and technologies also contribute to audit costs. Experienced auditors with in-depth knowledge of cybersecurity frameworks and industry best practices may command higher fees, while the use of advanced tools for vulnerability scanning, and risk analysis may incur additional expenses.
Balancing Costs and Benefits
While the costs of cybersecurity audits may seem daunting, they are an essential investment in protecting organizations against cyber threats and ensuring compliance with regulatory requirements such as the Essential Eight in Australia. By conducting regular audits, businesses can:
- Identify and mitigate vulnerabilities in IT networks.
- Enhance resilience against cyber attacks and data breaches.
- Demonstrate commitment to cybersecurity best practices and regulatory compliance.
- Safeguard sensitive information and maintain trust with customers, partners, and stakeholders.
Methodologies Employed by IT Networks
At IT Networks, we take a structured approach to cybersecurity audits, using industry proven methods to check and improve the security of our customers. When it comes to pricing our cybersecurity audit services, we’re all about being flexible and open. We provide customized solutions to fit the different needs and budgets of our clients. Here’s a quick look at how we do it, along with some estimated costs:
Initial Assessment and Scoping: At the start of the audit, we conduct a thorough initial assessment. We work closely with our clients to understand their specific business needs, goals, and current security setup. This helps us outline the scope and objectives of the audit. Best of all, this first step comes at no cost to you.
Risk Analysis and Threat Modeling: We analyze risks and model threats using a risk-based approach. This involves digging deep to uncover vulnerabilities and threats in your IT setup. We prioritize risks based on their likelihood and impact, focusing on the most critical areas. Afterward, we present the findings to you in straightforward PowerPoint slides, giving you a clear snapshot of your security status and risks. Here’s a sample for your reference:
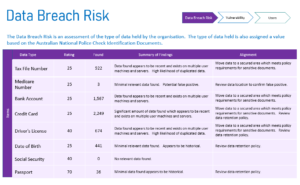
Equipped with cutting-edge tools, we conduct thorough data scans to assess the value and location of your data. The cost of these scans depends on the amount of data your organization holds and the number of devices it’s on. For instance, a company with 50 devices and 1TB of data would pay around $1,800 for the Data Breach Risk report. The cost of the Data Breach Risk Report is directly proportional to the number of devices and amount of data an organsation has. The pricing is tiered so it can vary. To calculate an indicative cost, use $50 per device scanned by the number of devices that you have.
We ensure compliance with industry standards like the Australian Cyber Security Centre’s Essential Eight. Our detailed assessments pinpoint any compliance gaps and offer practical solutions for improvement. Here’s an example of what you can expect:
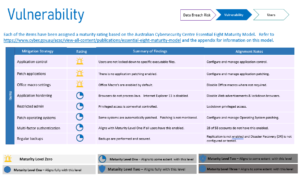
The cost to audit your environment and provide a vulnerability risk assessment is $4,800 for an organization with 50 staff members. Again, this figure varies based on the number of users that you have and is also tiered. Using a figure of $100 per user will provide an indicative cost.
Security Policy and Procedure Review: In our cybersecurity audits, we carefully assess your current security policies, procedures, and protocols. We evaluate how effective your existing policies are at reducing risks. Additionally, we offer any new policies needed to strengthen your security governance and align your organization with a Australian Cyber Security Centre Maturity Level. Completing a Security Policy and Proceedure review is a fixed cost of $2,200, regardless of the size of the organsiation.
After completing the audit, we present all findings to relevant stakeholders in a formal one-hour presentation. You’ll receive a clear roadmap outlining the necessary steps to take next. Here’s an example of what the roadmap looks like:
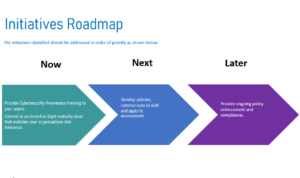
You won’t be charged for receiving the roadmap and presentation for your key stakeholders.
Cost Summary
For an organization with 50 users and 1 Tb of data, the total cost comes to $8,800 when considering all audit stages.
Breakdown:
- Data Breach Risk: $1,800
- Vulnerability Risk: $4,800
- Security Policy Review: $2,200
Keep in mind, the total cost may vary depending on whether your organization requires all three steps. Some clients we’ve worked with skip the Data Breach Risk analysis if they already know their data types. If needed, use $50 per device and $100 per user as estimates for Data Breach Risk and Vulnerability Risk, respectively.
What to Look out for
Cybersecurity audits are indispensable tools for organisations seeking to fortify their defenses against evolving cyber threats. By understanding the costs associated with these audits and the methodologies employed by trusted providers like IT Networks, businesses can make informed decisions to protect their valuable assets and data.
Choosing the right IT company to conduct your cybersecurity audit is crucial for several reasons:
- Expertise and Experience: Not all IT companies specialise in cybersecurity. Opting for a company like IT Networks with specific expertise in cybersecurity ensures that your audit is conducted by accredited professionals who understand the complexities of modern cyber threats and can provide relevant insights and recommendations.
- Tailored Solutions: Every organisation has unique cybersecurity needs and challenges. A specialized IT company like IT Networks can tailor the audit to address your specific requirements, providing customised solutions that effectively mitigate risks and enhance your security posture.
- Trust and Reputation: Entrusting your cybersecurity audit to a company like IT Networks with a proven track record instills confidence and trust. Working with a company that has a positive reputation in the industry reduces the risk of potential issues or conflicts of interest, ensuring that your audit is conducted impartially and ethically.
Ultimately, selecting the right IT company for your cybersecurity audit is an important decision that requires careful consideration. By choosing a company with the expertise, experience, and reputation to meet your specific needs, you can ensure that your audit is conducted effectively, providing valuable insights and recommendations to enhance your organization’s security posture.



